What is Application Modernization?
Application Modernization is process of updating or transforming existing legacy application to make them more efficient, scalable and cloud native. This approach of application modernization helps business to meet demands of modern customers and still remain competitive. What it involves is replacing older system to new ones, integration of new applications, development of new processes and workflows. Some of these approaches could include refactoring, re-platform which is include rebuilding entire application on Kubernetes.
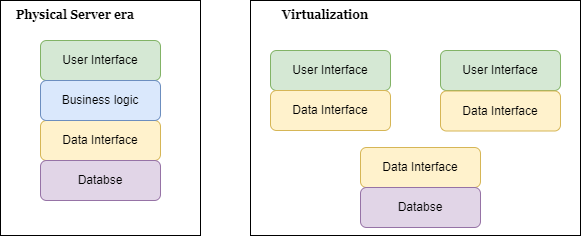
Motivation behind doing this is a problem with the legacy application, some of them are complex, outdated, and difficult to maintain. Also, it have been built on older technology platforms that are no longer supported or required manual processing with significant resources. For Example, DevOps platform with CICD pipeline can make process automated and probably you will not be able to do with legacy application.
Another disadvantages with legacy applications is, you may have limited scalability, poor performance and less security.
Difference between Legacy and Modern Application
| Legacy Application | Modern Application |
| Difficult to maintain | Significant investment in people |
| Difficult to update | Change in the processes |
| Less secure | Change of technology |
| Massive piece of software |
Ideal design for cloud is to break up everything into Microservices. The whole concept about moving from monolith to microservices and this smaller microservices need communicate with each others and fix the problems of legacy applications. Application Modernization offer benefits of Scalability, security and high availability. However, going on this journey is not as easy task, it requires significant investment in people to achieve desire outcomes. Right foundation must be established in the beginning to avoid high cost of re-architecture and it takes lot of efforts to migrate. Primary pain point is not just deciding what technology to adopt but to set proper migration process. It could major road blocker to achieve success in this path.
Let’s talk about Container Security.
Container Security
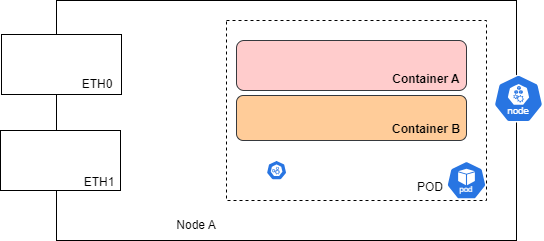
one of the key benefits of containerization is to package all the applications and dependency into smaller, portable and lightweight container images which can be shared and distributed within development team. By packaging application and it’s dependency within container image, you can ensure that your application is isolated from the host system. This is the basic difference between VM and containers. Although you shared a common kernel, it will help to reduce risk of security breeches. while creating container images, you will have to be careful to include only necessity components and remove unnecessary files, libraries, extensions and folders that are not required.
Here are the points to make sure for securing images
- Include your application in a container image
- Include as little as possible
- Scan your images
Make sure to use scanner to scan your container images for vulnerability.
Talking about Container images, you will have to know about Image registry. Let’s understand that.
Image registry
There are two types of registry for image. one is public and another is private. Depends on your organization specific requirements, you can choose one in public cloud providers. Public image registry is convenient for teams for smaller projects and open source software. Private image registry is necessary for larger enterprises that have very strict rules with respect to security and regulatory requirements. For example, Government agencies and Banks prefer to use private image registry for data protection and security compliance and they have sensitive information, they can control the access.
| Public Image registry | Private Image registry |
| Large community and ecosystem | Compliance |
| Ease of access | Greater control |
| Wide range of images available | Rquires configuration and maintenance |
| Cost effective | Can get expensive |
Network Segmentation
Network Segmentation is to provide isolation of your container at network level. Kubernetes network segmentation is the process of dividing the Kubernetes cluster’s network into smaller isolated segments. You can achieve this by setting network policies to restrict communications between different pods, services and namespaces.
Network segmentation is important for security purpose that helps to limit the potential impact to security breech. Assume that your application is already breach, if you have good network segmentation in place, what it does is prevent attacker to unable to access information.
Segmentation Tools
- Labels
- Security Policies
- Role based access control (RBAC)
Let’s look at best practices to be applied on Kubernetes environment.
Kubernetes Network Policy
Kubernetes has built in resource which is called Kubernetes Network Policy that can set security posture of your cloud native application. However, networking Kubernetes does not enforce these policies. You will have to delegate this function to CNI plugin and that is also the reason to must have CNI. These policy resources can be attached to namespaces and pods. You can do this either block or route traffic to workload. Policy resources are great tool but it has some limitation, won’t have explicit action attribute.
Monitoring
Let’s look at monitoring. It is very critical to have monitoring which can help you lot of security usecases. Monitoring is critical component for container security because it allows administrator to detect and respond security threat in real time. Also with Container, application is highly dynamic and distributed so pods can restart for some reason when it has some problem and that can fixed if you gain visibility on it’s behavior and easily mitigate to identified security issues.
Methods of Monitoring
There are two types of monitoring
- Infrastructure Monitoring
- Application Monitoring
1. Infrastructure Monitoring
with infrastructure monitoring, container rely on underline infrastructure such as host os, network and storage. There are infrastructure monitoring tools that can help detect any issues or detect vulnerability in infrastructure such as resource utilization, network latency and storage capacity. These are the things actually impact your container performance and security.
2. Application Monitoring
Application monitoring with helps to identify any vulnerabilities or issues within the application code deployed in container. There are application monitoring tools available which can help to detect leak or errors or application crashes. You can monitor to get comprehensive understanding of application health and environment.
That’s wrap up the whole flow of container security leading all the way to monitoring with application modernization.